Encrypted Keys, Terminal Servers (RDS) and VDI
Encrypted Keys, Terminal Servers (RDS) and VDI
License keys are encrypted using a machine-specific seed when they are applied. These seeds are used in a hash to dynamically decrypt the keys when PDF-XChange products attempt to validate their license status. Load-balancing RDS farms often run PDF-XChange products on different hardware from that used to apply the key, which results in the seed used to encrypt the key being unavailable at run time, the hash failing and the license reverting to "trial mode." A similar issue occurs when deploying VDI or imaged desktops - the seed used to encrypt the key when the master image was made is not available to the deployed instance, which results in the hash failing and the software reverting to "trial mode".
The XCVault.exe utility can be used to resolve these issues, as it decrypts the keys on the master instance and before being used to deploy to other hardware. This should be performed on the primary host on application of the license keys in the case of existing server farms, and on the master image (prior to deployment) in the case of VDI and Sysprep OS images..
Note
•Existing keys can be decrypted using XCVault.exe /OpenKeys
•New keys can be added without encryption using XCVault.exe /AddKeys /R. (Information about how to use the XCVault.exe utility are available here.)
Decrypting an Existing Key
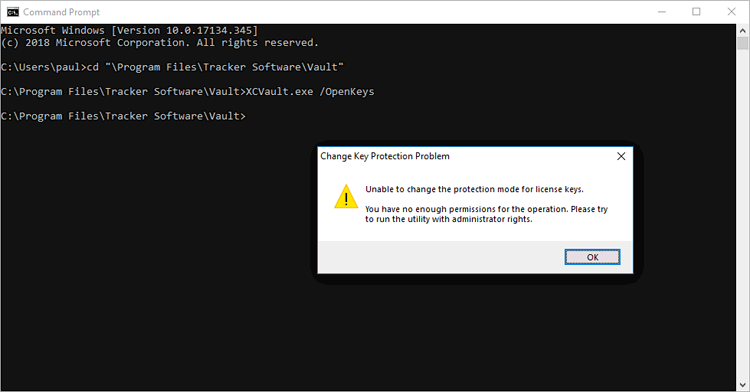
Decrypting a key requires administrative rights, regardless of whether the key is in HKLM or HKCU. Attempting to decrypt a user key without administrative rights will result in an error:
Figure 1. Error Message Displayed When Attempting to Decrypt a User Key without Administrative Privileges
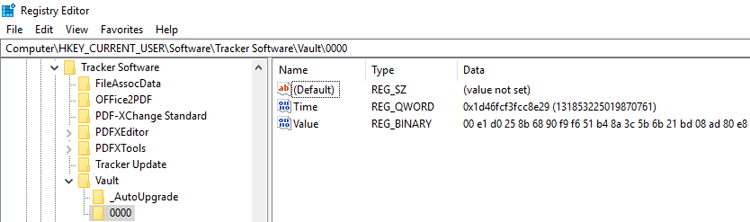
The key will remain encrypted in the user section of the registry:
Figure 2. Registry Editor, Encrypted Key
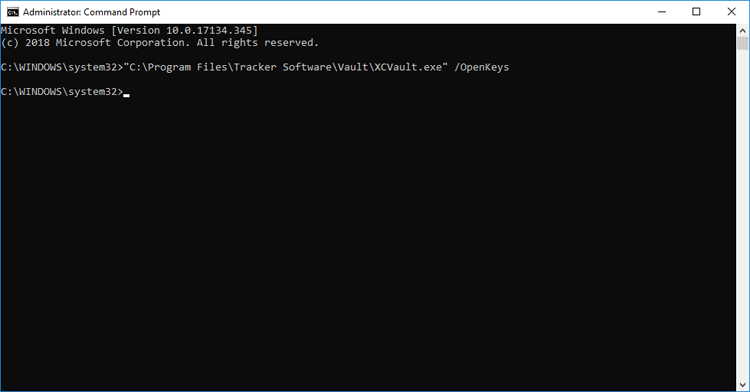
Running the command "C:\Program Files\Tracker Software\Vault\XCVault.exe" /OpenKeys from an elevated command prompt will succeed without any error messages:
Figure 3. Elevated Command Prompt, /OpenKeys Command Line
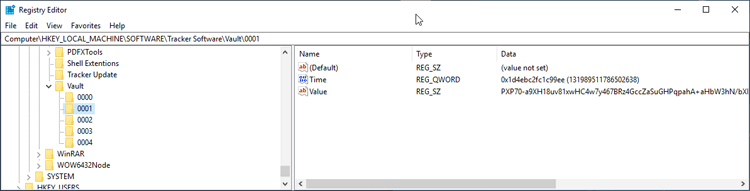
All keys in both HKCU and HKLM will be decrypted:
Figure 4. Registry Editor, Decrypted Key
This installation can now be used as a master image for deployment to other hardware.
Adding New Keys without Encryption
As well as decrypting existing keys, xcvault.exe can also be used to apply license keys to unlicensed machines, either encrypted (default) or not encrypted. Use the /S switch with /AddKeys for this to install keys without encryption.
/AddKeys
This command installs all license keys from .xcvault files.
Syntax
xcvault.exe [/AddKeys] <xcvault_file> [/M|/S|/R]
/M – specifies that new keys are added in the HKEY_LOCAL_MACHINE registry section and administrative rights are required.
/R – specifies that new keys will be unencrypted when added. Please note that this does not affect existing keys.
/S – specifies that the command is not permitted to show error/information messages.
Example
xcvault.exe /AddKeys "c:\Personal.xcvault" /M /R /S
Will install the key in HKLM, unencrypted, and without messages. (silent)