 Licensing
Licensing
PDF-XChange moved to a new serial key licensing system at build 308 of our products. The new system offers both the standard serial key method of licensing our applications as well as the option to use a license file. The license file is known as an "XCVault" file, which is a modified .zip file. The main benefit of this feature is that there is no longer a need to re-install the software if you are using an evaluation version and intend to upgrade. Follow the steps below to access and activate XCVault files:
1. Login to your account with PDF-XChange.
2. Move to the "Your products and Serial numbers" tab.
3. Move to the product for which you would like to download the XCVault file.
4. Click the arrow icon indicated in (figure 1). The window will expand as detailed below:
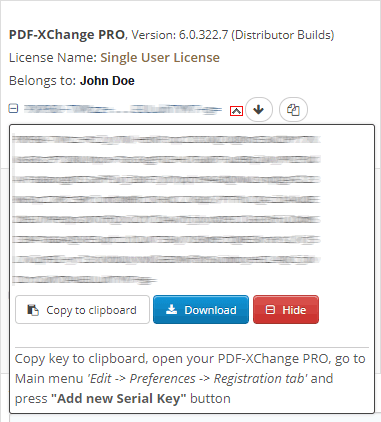
Figure 1. XCVault File Access Point
5. Click the Download button. The XCVault file will then download to the local computer.
6. Click the download icon to launch the XCVault file. All product licenses will then update automatically.
System administrators should note that this information is stored within the Windows registry. However, the method used to license the application can have an effect on the storage location. When an XCVault file is used, its information is stored in two locations: HKCU\Software\Tracker Software\Vault and HKLM\SOFTWARE\Tracker Software\Vault. It should also be noted that license information is stored as a hexadecimal value. Therefore, if a registration key is being used to deploy the license, it is advisable to first license a single machine in order to create the first registration key.
Standard Deployment
Copy and paste serial keys into the installer to implement them during installation. Alternatively, click the personal.xcvault file after installation has taken place.
Silent Deployment
XCVault files can also be used for silent deployment of serial keys after installation has taken place. A windows command line can be used to push the XCVault file to each user that qualifies for a full license. The command line for operation is: XCVault.exe /Option <path_to_xcvault_file>. Available command line options are detailed below:
XCVault Command Line Options
/s
Installs the software in silent mode.
/m
Per machine - administrative rights are required for this option.
/Install
This command designates the utility as the default handler of .xcvault files in the system. Please note that this requires administrative rights.
Example
xcvault.exe /Install
/AddKeys
This command installs all license keys from .xcvault files.
Syntax
xcvault.exe [/AddKeys] [/M|/S|/R] <xcvault_file>
/M – specifies that new keys are added in the HKEY_LOCAL_MACHINE registry section and administrative rights are required.
/R – specifies that new keys will be unencrypted when added. Please note that this does not affect existing keys.
/S – specifies that the command is not permitted to show error/information messages.
Examples
xcvault.exe /AddKeys "c:\Personal.xcvault"
xcvault.exe "c:\Personal.xcvault"
/OpenKeys
This command removes protection for all installed, protected license keys on the machine and converts them into unencrypted, readable text. Additionally, this command places a permanent flag in the system registry that forces all products from PDF-XChange to add new license keys without the standard encryption.
Please note that the software encrypts new keys by default for security reasons. Encrypted keys cannot be exported from the registry and used on other machines. Therefore this command is available only in special cases and may require administrative rights.
Syntax
xcvault.exe /OpenKeys [/M|/S]
/M – keys stored in HKEY_LOCAL_MACHINE registry section only will be converted. If this option is not specified then all keys in HKEY_CURRENT_USER and HKEY_LOCAL_MACHINE will be converted. If this option is not specified and the utility has no administrative rights then only the keys in HKEY_CURRENT_USER will be processed.
/S – specifies that the command is not permitted to show error/information messages.
Example
xcvault.exe /OpenKeys
/ProtectKeys
This command encrypts all installed license keys on the machine. Please note that administrative rights may be required to use this command.
Syntax
xcvault.exe /ProtectKeys [/M|/S]
/M – keys stored in HKEY_LOCAL_MACHINE registry section only will be converted. If this option is not specified then all keys in HKEY_CURRENT_USER and HKEY_LOCAL_MACHINE will be converted. If this option is not specified and the utility has no administrative rights then only the keys in HKEY_CURRENT_USER will be processed.
/S – specifies that the command is not permitted to show error/information messages.
Example
xcvault.exe /ProtectKeys
A sample script and associated literal path is detailed below:
C:\Program Files\Tracker Software\Vault>XCVault.exe /s with literal path D:\Documents\Ref\Personal.xcvault
Activating silent deployment is a two-step process. The first step is to call on the XCVault.exe that will apply the key. The second step is to specify the literal path to the personal.xcvault file. The presence of the script means that users are not notified of serial key deployment.
Passing License Details During Installation
The inclusion of XCVault files since build 308 means that the command line install option KEY=<regkey> no longer passes license details to associated products. The command line can be used to resolve this issue and there are two methods available:
The first method is to use the option KEYFILE=<xcvault file> to specify the UNC location of the license vault file <filename>.xcvault. For example:
KEYFILE="C:\Users\JohnDoe\Desktop\Personal.xcvault".
The second method is use the option KEYDATA=<regkey> to specify the registration key with a text string. For example:
KEYDATA="PXP70-Y5EN....cFrBqnyKhv7eOw=".
The first method is recommended as the new keys are very complex and therefore less suited to being passed as strings at the command line.